Double-Spending Problem and Byzantine General’s Problem in Relation to Cryptocurrency
Double-Spending Problem and Byzantine General’s Problem in Relation to Cryptocurrency
Counterfeiting, fraud, and even Ponzi Schemes are frequent headlines in today’s news. More importantly, these situations evidence one of the greatest flaws in today’s financial and recording systems: the double-spending problem and the Byzantine General’s Problem.
In the following article, we will describe the issues arising from these two problems, and how blockchain solves these concerns, making cryptocurrency one of the safest and most reliable assets for preventing these types of anomalies.
Problematic
Is it possible to copy gold, or reproduce it? Is it possible to turn one ounce of gold into two ounces, or even 1.1 ounces, without adding more gold? Of course not. This is one of the reasons that gold is a store of value and can be used in the exchange of goods.
But what about paper money? Is it possible to copy a dollar bill? Sure, but it may be tricky. In order to duplicate a dollar bill, one would need special equipment and the right kind of paper to do so. It would be difficult to create a sufficient duplicate using a normal photocopy machine. Moreover, there is no possibility of double-spending when using physical paper money because if an individual has a 100-dollar bill and hands over it to someone, the individual is left with nothing to double-spend.
However, this is not the case with digital money or assets, where a digital asset is a set of codes that can be copied and sent to several recipients. If anyone can easily copy or transmit it to others for transactional purposes, how is a digital currency even useful? If an individual or organization can easily duplicate his or her digital assets, his or her assets will eventually lose their value. For this reason, third parties, such as banks and PayPal, keep ledgers that guarantee that no double spending occurs. On the other hand, banks can print money out of thin air through their fractional reserves. Put simply, banks are authorized to lend $1.60 for every $1.00 that they have in reserve. But where does this $0.60 come from? It comes through a single computer command, eventually leading to the oversupply of currency and, ultimately, inflation.
Can there be double spending with cryptocurrencies? Most people now know that there are no third parties or banks involved in recording cryptocurrency transactions. In order to understand how blockchain provides a solution to these problems, it is necessary to understand the different types of transaction-recording methodologies that have been used for cryptocurrencies to this point.
The First Problem: The Three Record-Keeping Methodologies.
There are three basic methodologies used to record simple economic transactions. In the beginning, people used single-entry ledgers that contained information about the quantity of the goods being sold or purchased and their respective price. Although simpler in design, it was ultimately a very unreliable ledger. All anyone had to do was remove a few lines of entries before the funds were gone or missing from the records. No backup or verification of such transactions could be done on the back end.
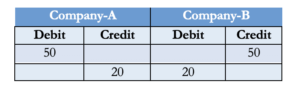
In order to resolve some of these issues, a new methodology was designed: the double-entry ledger. The double-entry ledger contains information about the amount spent and the amount earned. For this reason, bank statements today consist of numerous debit and credit records. This is the current method of choice. In fact, the modern monetary finance systems use double-entry systems as well. Even though these systems do a better job of recording transactions than single-entry systems, double-entry systems still fall victim to human error or greed, including Ponzi Schemes. In other words, double-entry systems trust even the fallible bookkeepers, messengers, and accountants.
Table 1: A typical double-entry ledger maintained by a third party
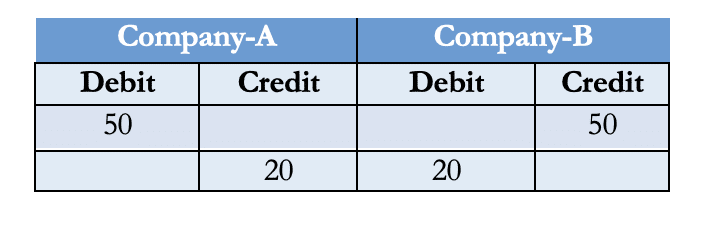
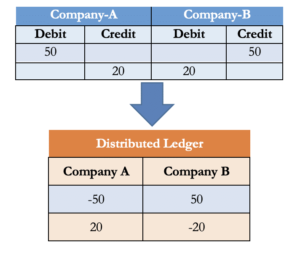
More recently, the triple-entry system has been introduced as a solution to all of these issues. Like a double-entry ledger, the triple-entry system creates debit and credit lines as well. However, the triple-entry system also adds a receipt of transactions to the ledger. In the case of cryptocurrency, this receipt of the transaction is signed using cryptographic signatures verified by the crowd, and a distributed ledger is generated when the third party cryptographically signs the accounting entries. Falsifying, destroying, or changing the cryptographically sealed entity is practically impossible. Why? The answer will be discussed in the “Byzantine General Problem” section below.
Table 2: A typical triple-entry system with distributed ledger technology
Before moving forward, it is important to understand what it means to double-spend in a digital transaction, particularly with regard to cryptocurrency transactions.
The Second Problem: Double Spending
In digital cash systems, double spending involves the same funds being sent to two recipients at the same time. Double spending is possible because it is almost impossible for a recipient to tell whether funds being spent have already been spent without the involvement of third-party verification service.
In digital-cash systems, ensuring that funds are not duplicated is of paramount importance. Digital cash systems will not work if X receives ten units but copies and pastes them ten times to create a total of 100 units. Digital cash systems will also not work if X sends the same ten units to Y and Z simultaneously. In other words, there must be a mechanism that ensures that funds in the system are not being double-spent. Two approaches can be used to prevent double-spending: the centralized approach and the decentralized approach.
– Centralized Approach
In general, the centralized approach is easier to implement. It involves one overseer who controls the issuance, distribution, and verification of money. Pretend Simon wants to receive $200 in digital cash. Provided that he has sufficient balance in his count, he will first inform the bank of his request. Simon will then randomly select ten numbers to assign each a value of $20 to. In order to prevent the bank from looking into specific units, Simon obfuscates the random numbers by attaching a blinding factor. He then turns over all of the data to the bank, which debits his account for $200, and signs a message certifying that each of the ten pieces of information is redeemable for $20. Next, Simon goes to Erick’s restaurant and purchases a meal for $20 by revealing one blinding factor to Erick so that he can redeem the bill. Erick must redeem the bill immediately with the bank in order to prevent Simon from spending that same bill with another merchant. Meanwhile, the bank will check to make sure that the signatures are valid. If everything checks out, the bank will credit Erick’s account $20.
Even though this setup is great for private transfers, it fails in resilience because the bank can be the central point of failure at any time.
– Decentralized Approach
In a decentralized approach, the bank is replaced with a blockchain, an open and decentralized ledger that is available to all users. Blockchains verify transactions using power-intensive algorithms, also known as proof-of-work systems. However, the decentralized approach faces one of the more trivial problems known as the “Byzantine General Problem,” described in more detail below.
The Third Problem: The Byzantine General’s Problem
The Byzantine General’s Problem can be understood by imagining a city that must be conquered. It cannot be conquered by merely attacking from one side because it has an adequate defense. However, if two armies were to attack from both sides, the city would be defeated easily. Knowing this, the generals decided to divide their army into two so that the armies could attack the city from both sides at once. However, the key is that both sets of armies attack the city simultaneously. If there is no digital communication between the two generals, it would be very difficult to ensure that both armies attacked the city at the same time. Even if the generals were to use a messenger to coordinate attacks, the generals may not be able to trust the messenger. If city security were to capture the original messenger and send a fake one to the other side, for example, the attack would be unsuccessful. Is there any way to authenticate a message without trusting the messenger?
Blockchain and Cryptocurrency As Possible Solutions
The solution to the Byzantine General’s Problem is not simple. Perhaps, a kind of encryption would help, where the generals shared some secret phrase that decoded and verified the authenticity of the underlying message.
In a computerized world, decoding simple algorithms is very easy. For this reason, the hashing algorithms proposed by Satoshi Nakamoto have been extremely helpful in increasing the complexity of these algorithms.
More specifically, Satoshi Nakamoto proposed a data structure known as the blockchain or a database where participants (nodes) run complex algorithms for solving various mathematical problems. Once a mathematical problem is solved, a block is created and communicated to the whole network.
Similarly, transactions initiated by end-users are also verified by these nodes. In fact, a transaction is not immediately added to the blockchain. It is only added to the blockchain after a node has created a block using extensive computing power. In exchange, the node is rewarded with digital currency. In addition, transactions are communicated over the network live, meaning that every computer on the network knows about every transaction as it occurs. If some intruder tries to communicate a false transaction or double-spend the same coins over the network, it will be rejected because the other nodes will invalidate it.
Cryptocurrency, therefore, is a practical way to get around the double-spending problem and the Byzantine General’s problem, since it relies on blockchain. Cryptocurrency uses complex algorithms or proof-of-work systems that prevent fraud and incentivize participants to act honestly. Put simply, the more participants and more blocks that are added on the chain, the less probability that a fake block can be added to the blockchain. Or, in words of Satoshi Nakamoto, “the probability of an… attacker catching up diminishes exponentially as subsequent blocks are added.”[1]
[1] Nakamoto, Satoshi. ¨Bitcoin: A Peer-to-Peer Electronic Cash System¨.p.3, 2008.