Anti-Collusion | What Is Obfuscation?
Anti-Collusion | What Is Obfuscation?
Cryptography Obfuscation
Ensuring secure communication has been the focus of cryptography obfuscation since its beginnings. Even today, smart devices, cloud computing, storage outsourcing, data mining, and web-based services have created the need to secure not only communications but also the computation behind it. Such a need is pressing, especially as malicious actors continue to test the integrity and privacy of communication, computation, and data with increasingly sophisticated techniques. In this article, we attempt to summarize some of the more recent theoretical findings of the research community in the field of “encrypting functionalities,” also known as “obfuscation.” More specifically, this article focuses on how obfuscation protects intellectual property by hiding the source code implementation details from those outside of the system.
What Is Code Obfuscation?
“Obfuscation” refers to something that is very difficult to understand. Therefore, code obfuscation refers to writing code for an application that is so difficult that even attackers have a difficult time understanding the code and breaking it. Put another way, the primary objective of code obfuscation is to muddy the logical implementation of an application’s code in order to make it more secure.
How Does Obfuscation Work?
Obfuscation depends on some simple but very reliable methods which, when applied together, provide a strong shield that protects the source of the code from attackers. Some methods target the lexical structure of the application while others target the control flow. For example, some methods allow the programmer to rename the functions, classes, and methods with less descriptive names that minimize the amount of information available to the attacker. Other methods allow the programmer to remove debug information, such as the type of the parameter, line number, or source file used, and even. Programmers may also remove java annotations, if helpful. In short, cryptographic obfuscation is used to hide the implementation of the source code by making it as complex and unconnected to the outside world as possible.What Is Cryptography?
“Cryptography” comes from the words “crypt,” meaning “hidden,” and“graph,” meaning “writing.” Cryptography is used to hide, or protect, the data by applying some sort of algorithm to it. Even though many believe obfuscation to be synonymous with cryptography, encryption, and hashing, this is not really the case.
Differences Between Hashing, Obfuscation, and Encryption:
- Hashing
Hashing is the ability to create semi-unique keys based on large amounts of data. In any given hash, collusion is bound to occur. Likewise, if two different types of data are calculating the same value of a hash, the hash key will likely be enormous in size. Hashing is a single-way algorithm and cannot be reversed.
From a technical perspective, hashing takes random input and produces a string of data of a fixed length with the following attributes:
- Each input will always generate the same output hash.
- Two inputs will never have the same output.
- Because hashes run one way, it is impossible to generate the input from the output hash alone.
- Even the slightest change in the input will change the output.
-
Obfuscation
Obfuscation involves trying to remove helpful signs, remove any extra spaces that may have been added for better readability, and make things complicated in order to make the code more difficult to follow. However, while obfuscation makes understanding the internal interface more difficult, it only provides a moderate level of security. Obfuscation simply complicates an attacker’s ability to understand an interface; it does not require any additional knowledge to undo.
Obfuscation is also used to make it harder to duplicate a given product by reverse engineering.
Still, it is important to remember that obfuscation is not a strong control, like encryption, but merely a hurdle. Like encoding, it can often be reversed by using the same method that was used to obfuscate it. Sometimes it is a manual process that takes more time and work.
For example, when obscuring a computer code, the result of the limitation must still be consumable by the computer, or the application will end the function (e.g., JAVASCRIPT OBFUSCATOR):
- Encryption
Encryption generally involves one of two models: private key encryption and public-key encryption. Private key encryption has both users operating the same secret key. In contrast, public key encryption has one user operating a one-way key to encrypt and the other user operating a private-receiver key to decrypt, and only the receiver needs to know the secret.
Encryption ensures that data is secure from third parties. More specifically, encryption transforms data into sequences that hide information from outside attackers.For this reason, people are now able to, among other things, securely send passwords through the internet. Examples of popular encryption software include AES, BLOWFISH, RSA.
Not all obfuscation is created equal. Poor-quality obfuscation software creates a problem for cryptographers by it generally only hiding a part of the program, while the inputs and outputs remain unprotected. On the other hand, high-quality obfuscation software is often used like a trading application, where owners obfuscate their trading algorithms and send them to their clouds or end users. If successful, the program should work without the customer ever knowing how it is working. Obfuscation ensures that the internal parts of the programs remain a secret.
What Is Cryptographic Obfuscation?
Cryptographic obfuscation is a branch of cryptography that attempts to replace user trust in the software with mathematics.
One traditional example of cryptographic obfuscation is one that most people see every day—password entry. If the program allows the user to create a password, the odds are that cryptographic obfuscation was involved on some level. For example, the below code displays the message, “Congratulations, you have entered the right password,” whenever users correctly enter intheir passwords:
//Check a password and print out congrats if it’s correct
//
checkpassword(string password) {
if (password == “9988899888”) {
print(“Congrats: ….\n”);
} else {
print(“Invalid password, fool.\n”);
}
}
However, this code is very easy to read, making it quite apparent how weak it is from a security standpoint: Any attacker could break this code in seconds, just by glancing at it. In cases like these, passwords can easily be retrieved due to the lack of encryption. This is where cryptographic obfuscation comes in.
In general, “obfuscation” refers to the use of ad-hoc methods that turn simple codes into a complex spaghetti codes. In some cases, important constants are cut off and transferred into the code. Some of the code may even be encrypted, although only temporarily, because the description keys are also transferred with the code so that the code can run as intended. Put simply, obfuscation focuses on hiding the complex contents of the file, interrupting it, and making it confusing to read, while encryption focuses on transforming the contents into an unreadable form.
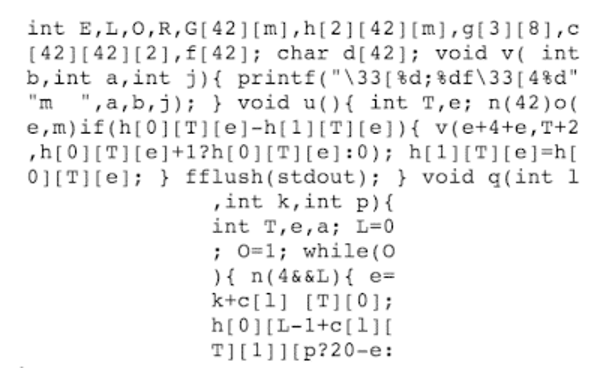
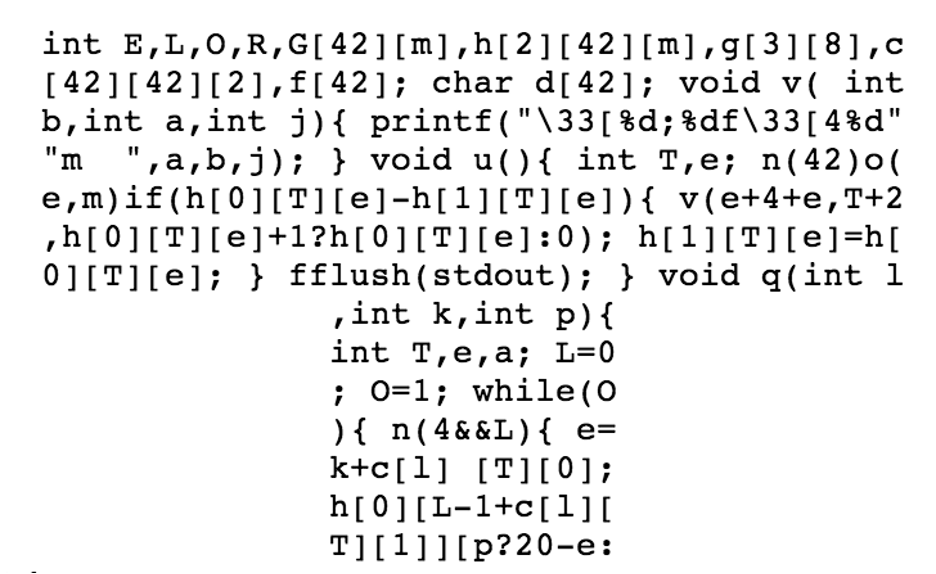
Pictured above is one of the winning entries from a 2013 obfuscation c contest.
Conclusion
Obfuscation methods are useful, but they are not the most secure solutions by any stretch. Obfuscation is neither “un-hackable” nor resistant to reverse-engineering processes. Given enough time and resources, an attacker is likely to get around some of the more common obfuscation methods, since such methods are not mathematically rigorous. Instead, obfuscation involves merely creating roadblocks in the process that are designed to slow down reverse-engineers and encourage them to give up.